Microsoft has begun deprecating TLS versions 1.0 & 1.1 across all services in Azure. This requires clients connecting to Azure resources to use TLS 1.2 at a minimum, preferably 1.3 if supported. While many deadlines have passed, Microsoft has extended support for Azure SQL until Aug 31, 2025.
What is TLS?
Transport Layer Security (TLS) is a security protocol that encrypts data between systems across a network. When you visit a website, and the URL begins with HTTPS, that site is securing the connection with TLS. The same applies when connecting to a SQL database.
Why the change?
TLS was first developed in 1995 as a Secure Sockets Layer (SSL). SSL was highly vulnerable to attacks and was replaced by TLS in 1999 with version 1.0. As security threats evolved, new versions were implemented to secure weaknesses, and TLS 1.0 & 1.1 were both officially deprecated in 2021. Though deprecated, organizations could still use these older versions, but they would no longer be supported. Many major technology companies began planning to phase out versions 1.0 & 1.2 while delaying enforcement to allow those systems to be updated. Considering the vulnerabilities of these deprecated versions, it is becoming a requirement to make the jump so companies can protect themselves and their customers. Many companies also have security standards that must be met, and TLS 1.2/1.3 is often required to meet those requirements.
What services are impacted?
Azure offers three options for running SQL.
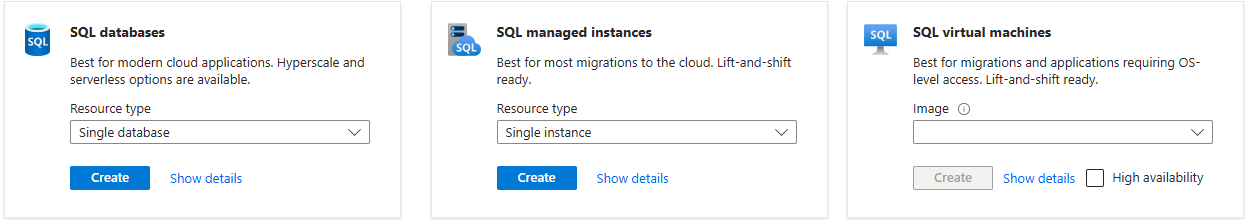
- Azure SQL Database is a fully managed serverless option where Microsoft can enforce the minimum TLS version.
- Azure SQL Managed Instances run on managed virtual machines. You have more options than SQL Database, but Microsoft can still enforce a minimum TLS version.
- SQL Virtual Machines are a traditional setup for hosting SQL Server on a virtual machine that the user manages. The user is responsible for all aspects of the VM, including the OS, TLS, and updates. This service is NOT affected by the deprecation change, but it is strongly recommended to enforce TLS 1.2.
How to prepare?
To ensure compatibility with TLS 1.2, keep any software making connections to SQL up to date. Most modern applications and software support TLS 1.2 by default. This includes SQL Server Management Studio, operating systems & devices.
TLS 1.2 is supported by the following operating systems (OS):
- Windows: Windows 7 was the first to support TLS 1.2 with manual configuration changes. Windows 8 enabled TLS 1.2 by default.
- Windows Server: Windows Server 2008 R2 supported TLS 1.2 with manual configuration. Windows 2012 R2 was the first to enable it by default.
- macOS: TLS 1.2 was enabled by default, starting with OS X 10.9 (Mavericks).
- Linux: Most modern distributions of Linux after 2012 include TLS 1.2.
Once your systems are updated to support TLS 1.2, you can monitor incoming connections to identify any still using TLS 1.0 or 1.1.
Azure SQL Database
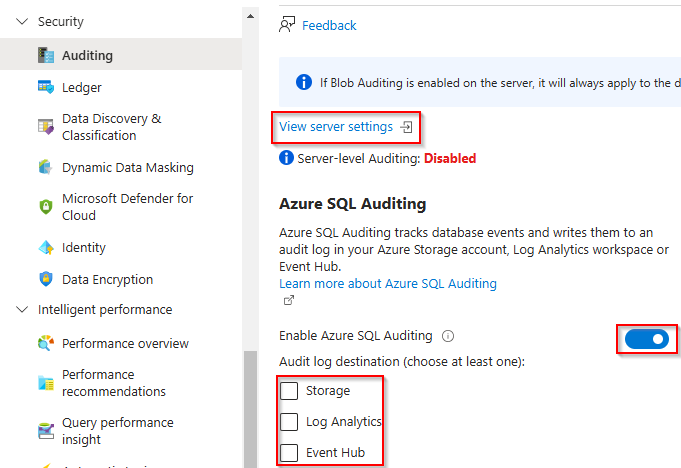
Turn on auditing for both the database & server. This can be done by going to each resource, expanding the Security blade on the left, and choosing Auditing.
To enable auditing at the server level, click on the View server settings link.
- Toggle the Enable Azure SQL Auditing option to on and select a log destination.
- **The easiest way to determine which TLS versions are in use is to use Log Analytics as a destination.**
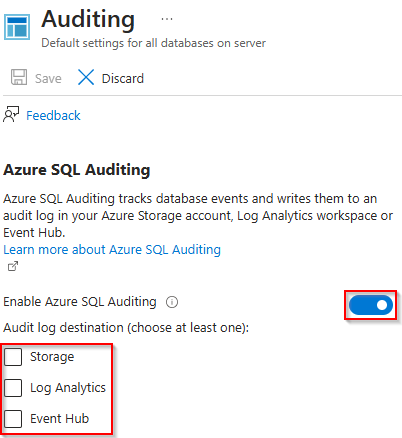
- Click Save. Once save is done, go back to the Auditing page.
- On the main Auditing page, click on View audit logs at the top.
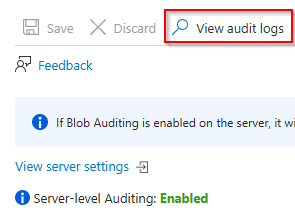
- On the main Audit records page, select Log Analytics.
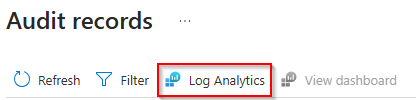
- On the main Audit records page, select Log Analytics. This will bring up the Logs where you can use a KQL query to find TLS versions that clients are using.
- Choose KQL Mode from the drop-down. Now you can run queries against the logs and find any clients that may still be using old TLS versions.
Some useful queries:
// Show all logs and columns
AzureDiagnostics
// Find all TLS versions being used
AzureDiagnostics
| distinct client_tls_version_name_s
// Find logs using specific TLS version
AzureDiagnostics
| where client_tls_version_name_s == '1.1'
// Find clients using specific TLS version
AzureDiagnostics
| where client_tls_version_name_s == '1.1'
| project Resource, host_name_s, client_ip_s
// Summarize clients using specific TLS version
AzureDiagnostics
| where client_tls_version_name_s == '1.1'
| summarize count() by Resource, host_name_s, client_ip_sTo enable auditing at the database level, toggle the Enable Azure SQL Auditing option to on and select a log destination. Follow the same steps as database Auditing to view the logs.
Azure SQL Managed Instance
Microsoft does not provide a way to audit connections or monitor TLS versions for SQL Managed Instance within Azure. Instead, it must be done inside of the SQL database itself. The process requires several steps.
- Create a storage account to store the data.
- Generate a Shared Access Signature (SAS) token to grant SQL access to the storage account.
- Create a credential in SQL to use the SAS token.
- Use the credential & storage account with SAS to create an Extended Events Session.
- Query the Extended Events Session.
What to change in Azure?
No immediate changes are required in Azure SQL. Microsoft will automatically enforce TLS 1.2 after August 31, 2025. However, it’s best to manually enforce TLS 1.2 now for a smooth transition.
Azure SQL Database
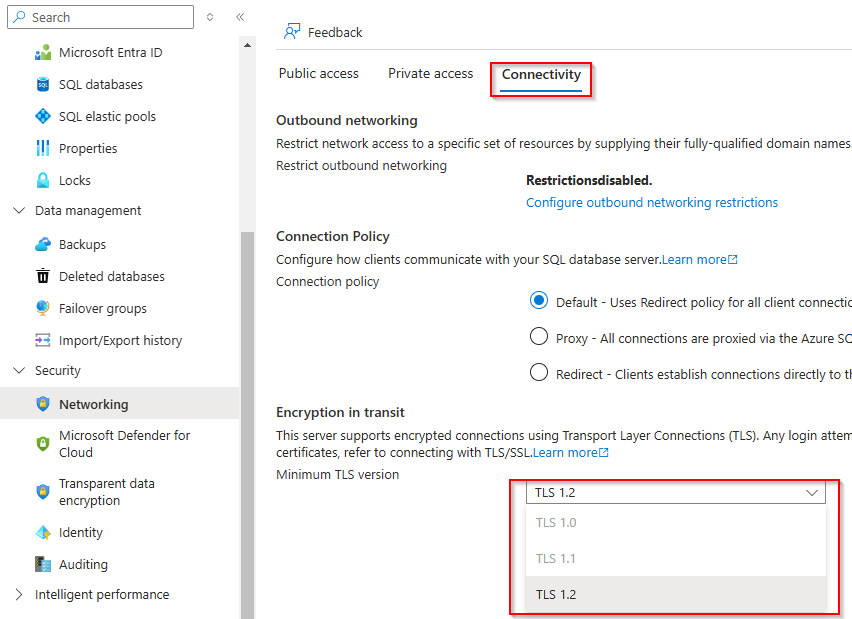
Go to each SQL Server hosting database, expand the Security blade on the left, and choose Networking.
Choose Connectivity from the top menu.
Under Encryption in transit, select TLS 1.2 from the drop-down menu.
Azure SQL Managed Instance
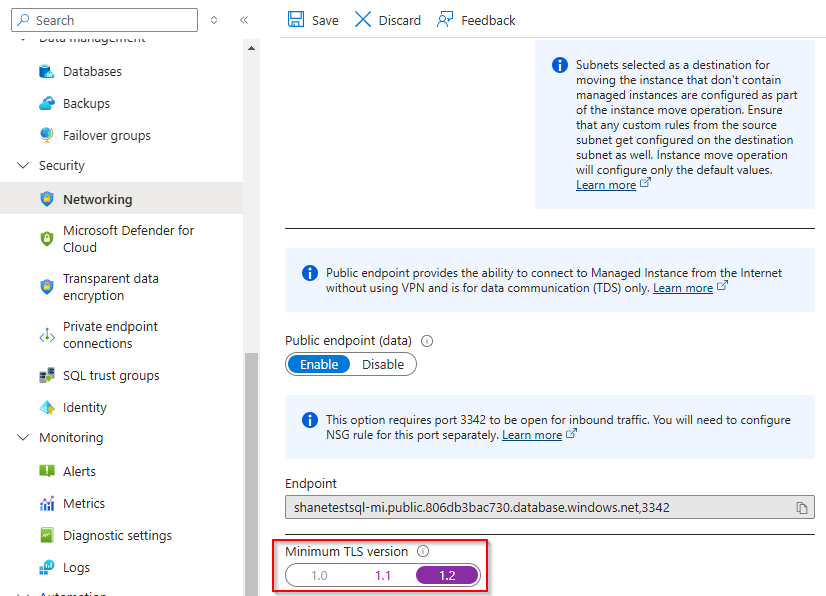
Go to each SQL Managed Instance, expand the Security blade on the left, and choose Networking.
Under Minimum TLS version, select TLS 1.2 from the options.
Notes
Any new SQL databases or Managed Instances created today will only allow TLS 1.2.
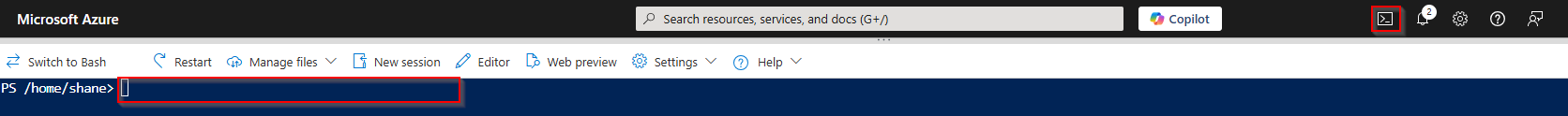
After setting TLS 1.2 for an existing SQL service, you cannot revert back to a lower version via the portal. If you need to revert back for any reason, you must do it via PowerShell or Azure CLI.
- The easiest is to use Cloud Shell in the portal. Choose the Cloud Shell icon on the top menu bar to do so.
PowerShell commands:
// Update Minimum TLS Version for SQL Server
Set-AzSqlServer -ServerName sql-server-name -ResourceGroupName resource-group -MinimalTlsVersion "1.1"
// Update Minimum TLS Version for Managed Instances
Set-AzSqlInstance -Name sql-instance-name -ResourceGroupName resource-group -MinimalTlsVersion "1.1"Azure CLI commands:
// Update Minimum TLS Version SQL Server
az sql server update -n sql-server-name -g resource-group --set minimalTlsVersion="1.1"
// Update Minimum TLS Version for Manged Instances
az sql mi update -n sql-instance-name -g resource-group --set minimalTlsVersion="1.1"For more information, please contact us or check out our Azure Managed Services.
This post was originally posted here.

